Typical VPN Implementations
There are many types of
VPN implementations, each with its own specific set of technology requirements. However,
VPN deployments can be grouped into three primary categories:
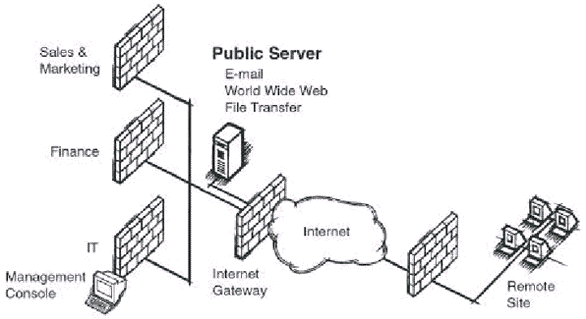
In Intranet VPNs that facilitate secure
communications between a company’s internal departments and its branch offices (see
Fig. 1), the primary technology requirements are strong data encryption to protect
sensitive information; reliability to ensure the prioritization of mission-critical
applications, such as ERP systems, sales and customer database management, and document
exchange; and scalable management to accommodate the rapidly growing number of new users,
new offices and new applications.

Fig. 1 Intranet VPN
Remote Access VPNs between a
corporate network and remote and/or mobile employees (see Fig. 2) have different
requirements. Strong authentication is critical to verify remote and mobile users’
identities in the most accurate and efficient manner possible. On the management side,
Remote Access VPNs require centralized management and a high degree of scalability to
handle the vast number of users accessing the VPN.

Fig. 2 Remote Access VPN
Finally, Extranet VPNs between
a company and its strategic partners, customers and suppliers (see Fig. 3) require an
open, standards-based solution to ensure interoperability with the various solutions that
the business partners might implement. The accepted standard for Internet-based VPNs is
the Internet Protocol Security (IPSec) standard. Equally important is traffic control to
eliminate bottlenecks at network access points and guarantee swift delivery of and rapid
response times for critical data.
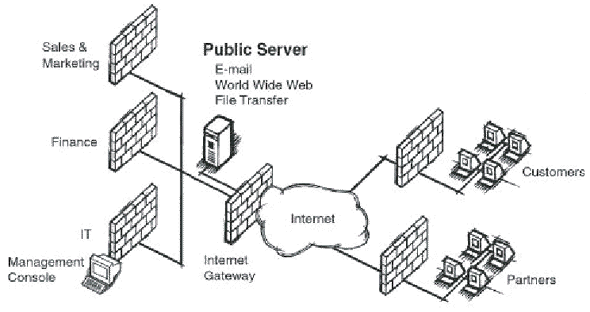
Fig. 3 Extranet VPN
Since VPNs represent only one
component in an overall security policy, the challenge is to provide a comprehensive,
integrated solution. "One size fits all" just doesn’t apply in the VPN
market. Most VPN vendors today provide solutions tailored to only one of these VPN
implementations. This is where the problem lies, since most companies have many
remote offices to connect together securely, along with an increasingly mobile workforce,
and a desire to leverage the Internet to get closer to customers and business partners.
Therefore, a VPN solution must support all three of the above applications, allowing
offices worldwide to access network resources, mobile workers to link up to corporate
intranets, customers to place orders and suppliers to check inventory levels, all in a
highly secure and cost-effective manner. While a corporation may only plan to implement
one of the three types of VPNs today, it is imperative that the VPN solution it selects
provide the ability to add either or both of the remaining two types seamlessly and easily
(see Fig. 4).
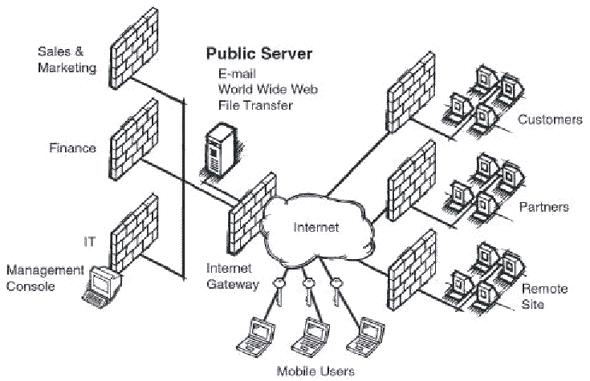
Fig. 4 A Complete VPN Implementation for Intranet,
Extranet and Remote Access Applications